Attack Surface Management for
Information Technology
Information is a magnet for cyber criminals, making both the actual products in the IT industry, such as hardware and software, and service organizations that provide network maintenance, business process outsourcing, and system support key targets. In theory, the IT industry has the knowledge and tools needed to fight cyber crime, but in practice, it is extremely vulnerable.
The first problem is the rate of change and development. The IT industry changes so quickly, that no company can keep up with all of the changes and the ever-evolving attack surface in-house. Forced to rely on third-party products and services, they are only as secure as their weakest link. Even within an organization, the relentless pace of development and the pressure to beat competitors to market can cause companies to overlook security.
Another problem is the need for remote access. Whether it’s the trend towards working from home and BYOD, or hidden backdoor programs that allow companies to access their products for service, remote access gives cyber criminals a way into IT products and systems.
IT companies and professionals need a simple way to see the big picture, and an automated tool to secure their attack surface, and track vulnerabilities and risk before they impact the system.
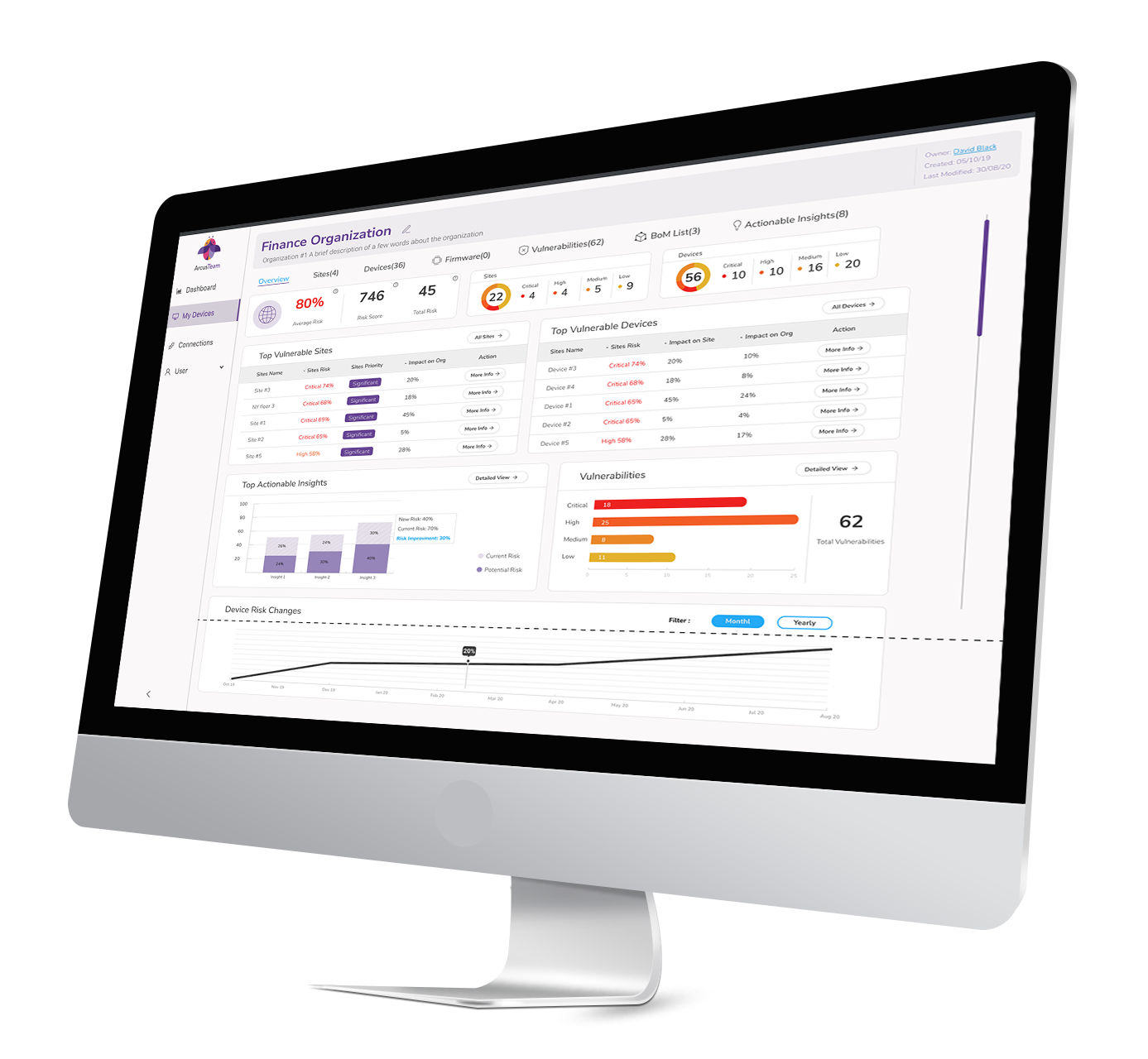
Centralized View for all Devices
DeviceTotal gives CISOs and cybersecurity teams at financial institutions and banks full visibility into their attack surface and all connected devices in their network, including their location, hardware, firmware, and software components. With this visibility, they can manage device security from anywhere in the world.
Using the platform’s centralized dashboard, the CISO has a direct line of sight (in one view) for every single device that is connected to the institution’s network, regardless of its vendor. Using this neutral, unbiased approach, the CISO and cybersecurity team can proactively protect the network against threats originating from both known and unknown vulnerabilities and in all connected devices.
Contextual Risk Prioritization
DeviceTotal also analyzes how threats translate into business risks for financial institutions and banks, and which threats are most likely to be exploited. Equipped with these invaluable insights, the CISO and cybersecurity team members can collaborate and focus their efforts on mitigating the most critical threats based on parameters such as device location, business context, risk level, and potential impact, and communicate progress to relevant stakeholders. DeviceTotal then takes attack surface management one step further by providing focused and clear security recommendations based on risk levels and prioritization, including recommended firmware updates and security patches.
Streamlining And Cost Savings
These recommendations eliminate the need to manually review and prioritize never-ending lists of recognized vulnerabilities. With DeviceTotal, the CISO and cybersecurity team can use accurate and actionable insights to make informed decisions about mitigating potential threats. In addition to saving time and costs, this significantly reduces the reaction time and enables the cybersecurity team to stay on top of the financial institutions’ network security and attack surface management needs at all times.

