DeviceTotal Platform
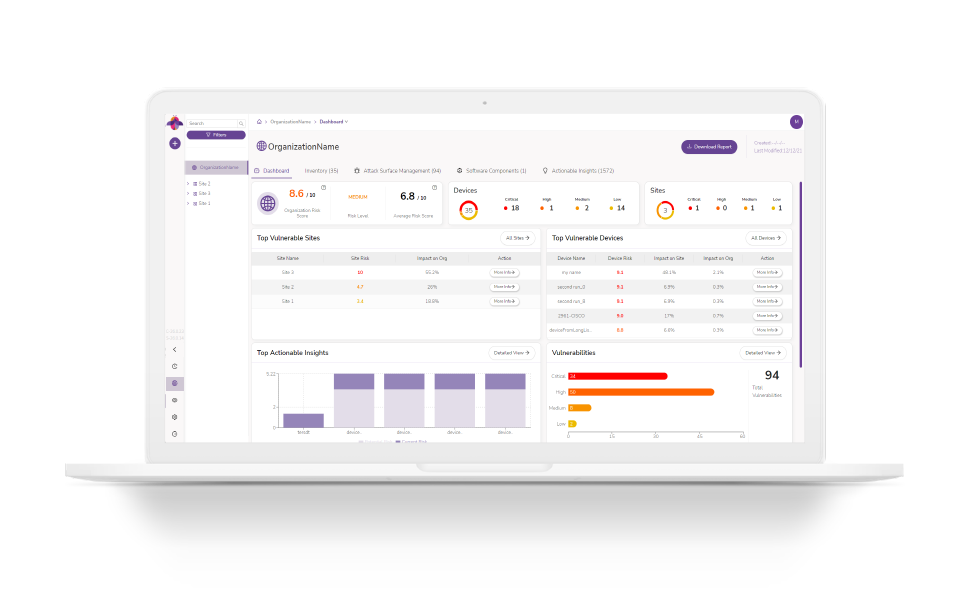
DeviceTotal identifies security threats, automatically highlights the risk, and provides actionable insights for swift and proactive mitigation.
It’s completely agentless, with no network installation, and provides in-depth risk analysis based on security data analyzed and structured directly from the vendors.comprised of security recommendations contextualized to your business requirements, giving you the control to prioritize your response to device-level threats and monitor the impact of mitigation
Gain complete protection for your connected, IoT and cloud devices:
DeviceTotal Protects your Devices and Organization from Cyber risks

Pre-purchase
Threat detection prior to deployment

Predictive
Identify known vulnerabilities and potential zero days

Proactive
Supports decision-making and resource prioritization

Precognitive
Threat detection prior to deployment

Predictive
Identify known vulnerabilities and potential zero days

Proactive
Supports decision-making and resource prioritization

Comprehensive
Device, site and organization-level analysis
Agentless
Nothing to install

Granular
Firmware and software risk identification

Comprehensive
Device, site and organization-level analysis
How does DeviceTotal work?
DeviceTotal’s proprietary technology automatically identifies security issues, analyzes the risk and offers recommendations to shore up connected device security, even before you purchase devices

Analyze
Analyze the attack surface score and risk metrics for every connected device on the network by identifying vulnerabilities and risk score
Calculate
Identify the device and network risk and visualize the entire nature of the attack surface posture in a contextual way for your organization
Mitigate
Access clear actionable insights - security recommendations that include recommended software updates and workarounds, directly from the vendors
Control
Prioritize responses based on organization, site, or device-level business context, risk, impact, and more, and monitor the effect of your actions
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
