Bridging the CVE Gap: Why Organizations Can’t Rely on NVD Alone — and How DeviceTotal Closes It
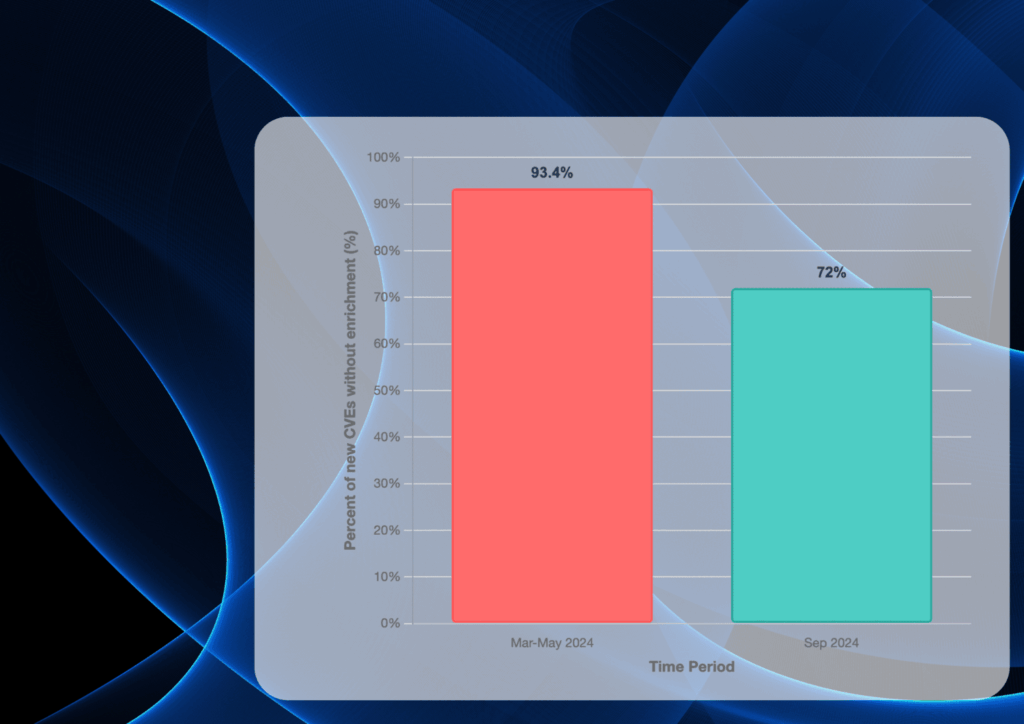
Bridging the CVE Gap: Why OEMs Can’t Rely on NVD Alone — and How DeviceTotal Closes It Forget half-measures — DeviceTotal is redefining device risk intelligence with unmatched accuracy and speed. Here are four standout wins from countless success stories: On Cisco IOS 15.9(3)M3, DeviceTotal mapped 31 CVEs—35 % more than NVD’s 23 — and instantly resolved 24 CPE misassignments (77 % false negatives/false positives), versus NVD’s four-month correction lag. JTEKT PC10PE-1616P (JVN and NVD): Public feeds reported 3 CVEs; DeviceTotal found 5 — a 66 % uplift. These vulnerabilities are still missing from JVN/NVD. Fortinet FortiGate 200F: NVD missed CVE-2025-22862 entirely; DeviceTotal surfaced it on disclosure, delivering 4.3 % more CVEs with full remediation guidance. This vulnerability is still missing from the NVD. These highlights are just the tip of the iceberg. With 100 % vulnerability coverage, insights from the day of disclosure, and rich operational context — EoL dates, vendor-recommended remediation and mitigation, latest versions, and actionable insights — DeviceTotal empowers you to remediate faster, smarter, and with absolute confidence. Capability NVD DeviceTotal Advantage Vulnerabilities Covered ~50–60 % of firmware CVEs ✅ 100 % of vendor disclosures (incl. non-CVE advisories) +40 – 50 percentage points uplift Extra vulnerabilities beyond public feeds 0 % ✅ 100 % (e.g. +2 JVN CVEs, CVE-2025-22862) Reveals hidden vulnerabilities CPE Mismatch Resolution 1 to 4 months or longer ✅ Resolves 100 % of misassignments Eliminates blind spots False Negatives 4.2 – 25.8 % (case-study range) 0 % No missed exposures False Positives Up to 77.4 % 0 % No wasted triage What Organizations Get Beyond Data Available on NVD and Other Public Databases Even when NVD lists a CVE, it typically does not provide the operational context organizations need to act quickly and correctly. DeviceTotal adds the missing, vendor‑aligned layers. Capability NVD DeviceTotal Advantage EoL/Lifecycle ❌ ✅ +40 – 50 percentage points uplift Mitigation/Workaround links ~ (sporadic) ✅ Reveals hidden vulnerabilities Fixed-firmware mapping ❌ ✅ Eliminates blind spots Normalized risk ~ (partial) ✅ No missed exposures Prioritization Up to 77.4 % ✅ No wasted triage Time-to-insight 60-120 days From the moment of vendor disclosure Instant actionable insights The problem: NVD enrichment backlog → systematic mapping errors Over 2024–2025, a large share of CVEs entered the NVD without enrichment (no CVSS, no CPE product mappings, and often marked “Awaiting Analysis”), and many stayed that way for months. Independent measurements found that 93.4% of CVEs published after Feb 12, 2024 were still unanalyzed as of May 19, 2024; by Sept 21, 2024, 72.4% (≈18,358 CVEs) remained unanalyzed, including 46.7% of Known‑Exploited CVEs. FIG-1: NVD Backlog Indicators: The bars show the share of new CVEs lacking NVD analysis (i.e., missing CVSS, CPE, or marked Awaiting Analysis). When these fields are absent or late, device/firmware matching breaks, yielding the misses and mis‑mappings seen in the case studies. While NVD hasn’t published an official 2025 percentage, NIST’s March 19, 2025 update confirmed processing had resumed but the backlog was still growing, and contemporaneous reporting put the queue at roughly 25,000 unprocessed CVEs in March 2025. DeviceTotal Case Studies Prove NVD’s Coverage Gaps Public feeds fall short. Missing CPEs, analysis delays, and version mismatches in NVD create critical blind spots and generate false positives, hampering device teams’ ability to act. DeviceTotal delivers exact device risk intelligence, updated daily directly from vendors. Across every case, we achieved 100 % recall and provided the operational context — official EoL timelines, vendor-verified mitigations, fixed-firmware mappings, normalized risk scores, and prioritized actions. Case study A — Eliminating Blind Spots for Cisco IOS 15.9(3)M3 While NVD took four months (Feb 5–Jul 2, 2025) to correct its mappings, DeviceTotal instantly flagged 31 CVEs on IOS 15.9(3)M3 — including 24 CPE misassignments (77 % false negatives on the correct train and 77 % false positives on the wrong one). Where NVD’s recall lagged at 74.2 % (missing 8/31), DeviceTotal delivered 100 % recall and zero noise from day zero. FIG-2: Cisco CVE coverage: Bars are counts mapped to IOS 15.9(3)M3 during the window. The callout (+34.8%) shows the uplift vs NVD at that time. FIG-3: Cisco recall on IOS 15.9(3)M3: Recall = TP/(TP+FN) on the correct firmware. NVD’s 74.2% vs DT’s 100% highlights missed exposures (NVD FN=25.8%) that DT caught. FIG-6: CPE mismatch impact on M3: The single column is 100% of M3’s true CVE set (31). It splits into Correct (7) vs Misassigned (24) → labels at top show Recall 22.6% and FNs 77.4%. Case Study B: JTEKT PC10PE-1616P CVE Discoveries A Japanese client used local intelligence (JVN/JPCERT) to scan its JTEKT PC10PE-1616P device. NVD reported 3 vulnerabilities, which was also confirmed by JVN, leading to an apparent “compliant” status. DeviceTotal’s research uncovered 2 additional CVEs (MTTT261501, MTTT261502), bringing the total to 5 — a 66 % increase over JVN/NVD. Public databases offered no remediation guidance, leaving high-severity risks unaddressed; DeviceTotal delivered vendor-verified fixes and full operational context immediately. FIG-7: This graph shows the jump from 3 to 5 vulnerabilities, highlighting DeviceTotal’s ability to reveal hidden vulnerabilities. Case study C — Uncovering a Fortinet FortiGate 200F (FortiOS 7.0.16) Missing CVE For FortiOS 7.0.16, DeviceTotal found 24 CVEs versus NVD’s 23 — a 4.3 % uplift. Notably, CVE-2025-22862, disclosed by Fortinet on June 10, 2025, still had no entry in NVD as of late July, yet DeviceTotal surfaced it immediately with vendor-verified remediation guidance. FIG-4: Fortinet CVE coverage comparison: Two 100% bars: NVD 95.8% covered / 4.2% missed (CVE‑2025‑22862) vs DeviceTotal 100%; +4.3% badge = DT 24 vs NVD 23. This case is not about “just one more CVE.” The point is that CVE‑2025‑22862 remains practically invisible to any NVD‑only workflow. It was reserved by MITRE on Jan 8, 2025 and disclosed by Fortinet on Jun 10, 2025 via FortiGuard/PSIRT, yet NVD still has no entry as of Jul 29, 2025 (“CVE ID Not Found”). That means no NVD CVSS, no CPE mapping, no references — so scanners, SBOM enrichment, and dashboards that depend on NVD won’t see it at all, while DeviceTotal does, because of its vendor-first approach. Read the full case study here.
