How To Submit Devices To DeviceTotal Community Edition
With DeviceTotal Community Edition, you can evaluate the risk posture of your OT, IoT, network, and security devices — free of charge and without installing anything.
You can submit:
- Up to 3 devices per request
- 1 request per week
- Up to 5 requests per month
Whether you’re analyzing existing assets or evaluating devices before purchase, Community Edition gives you vendor-verified, firmware-level security intelligence — including vulnerabilities, EoL data, and mitigation options — to help you make confident decisions.
Here’s how the submission process works and why each step matters.
Step 1: Enter Your Contact Information
We ask for your name, email, and company to:
- Deliver your personalized trial results
- Follow up with any clarifying questions
- Ensure your submission is tied to the correct device risk context
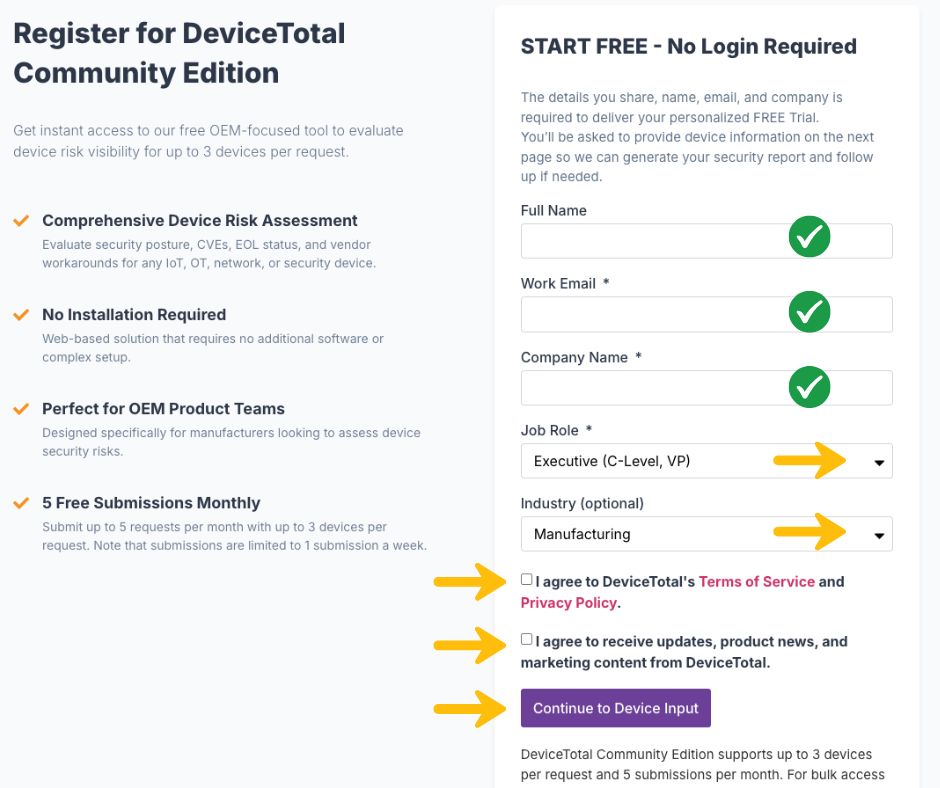
This information is never shared or used for any purpose beyond your trial experience.
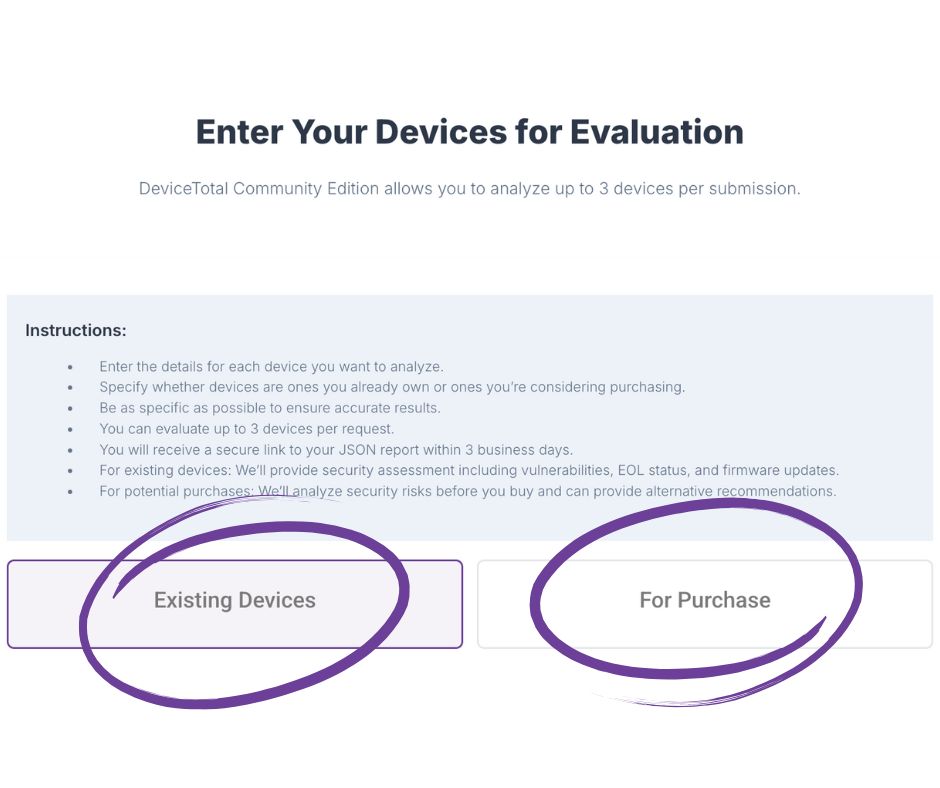
Step 2: Select Device Use Context
You’ll indicate whether your device is already in use or being evaluated for purchase. This helps us:
- Understand its operational context
- Provide recommendations for alternative devices in case of purchase
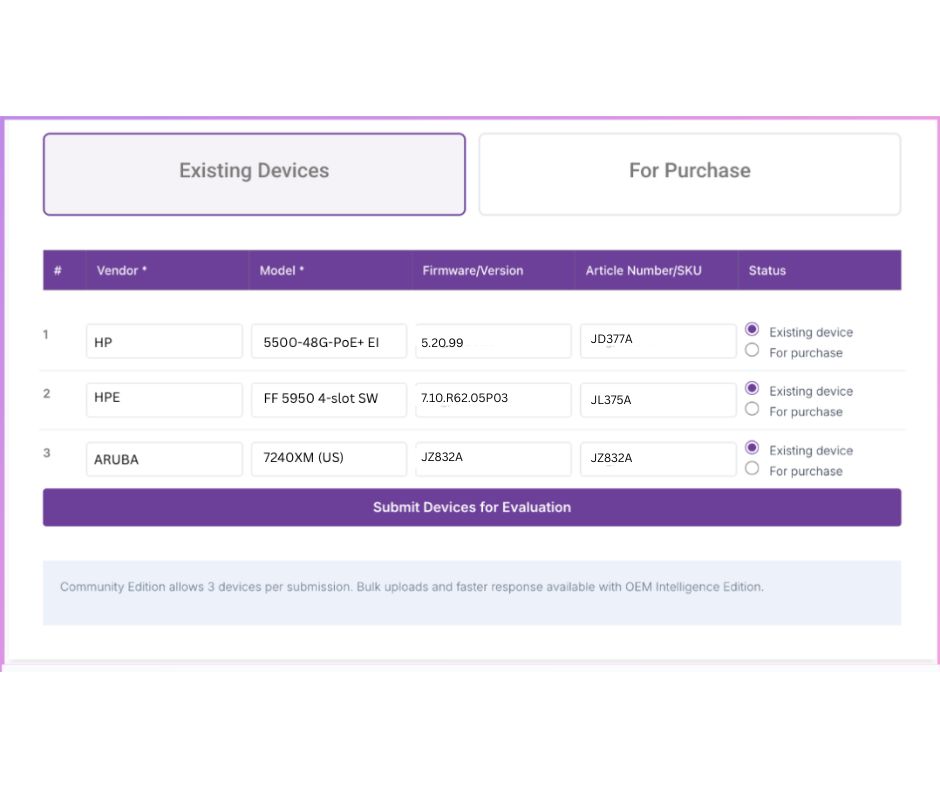
Step 3: Submit Device Information
Now you’ll enter as much device data as you have, including:
- Vendor name
- Series or model
- Firmware version (critical for accuracy)
- SKU number (optional, but useful for deeper matching)
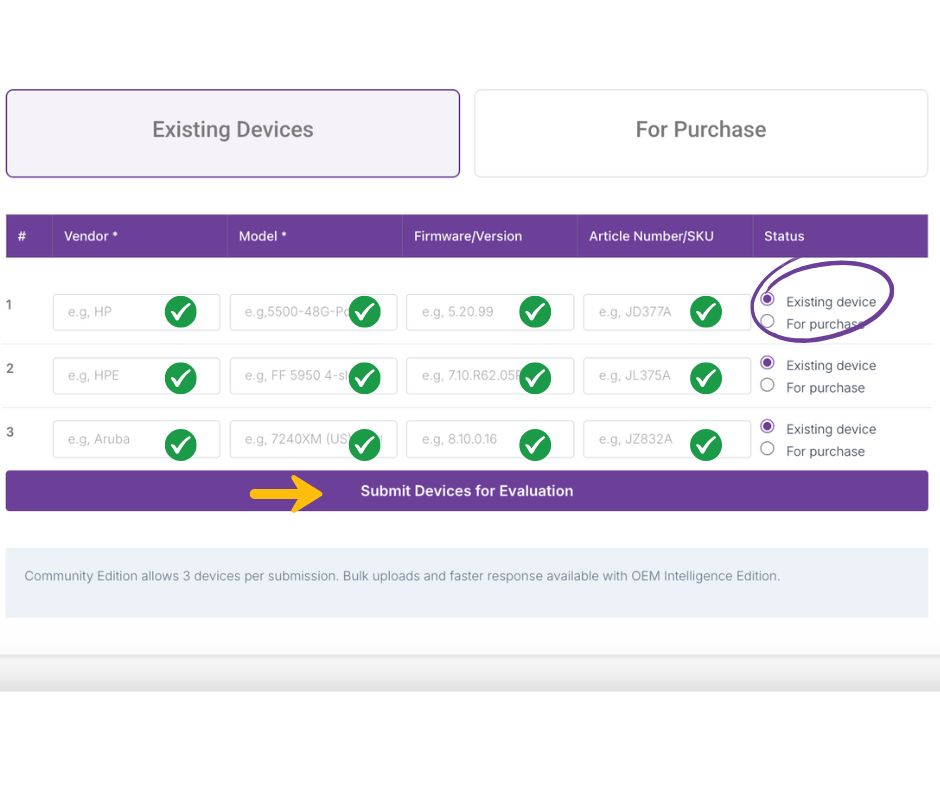
After you’ve entered the information, click the “Submit Devices for Evaluation” button. Your evaluation is sent for processing — and within 3 business days, you’ll receive your results.
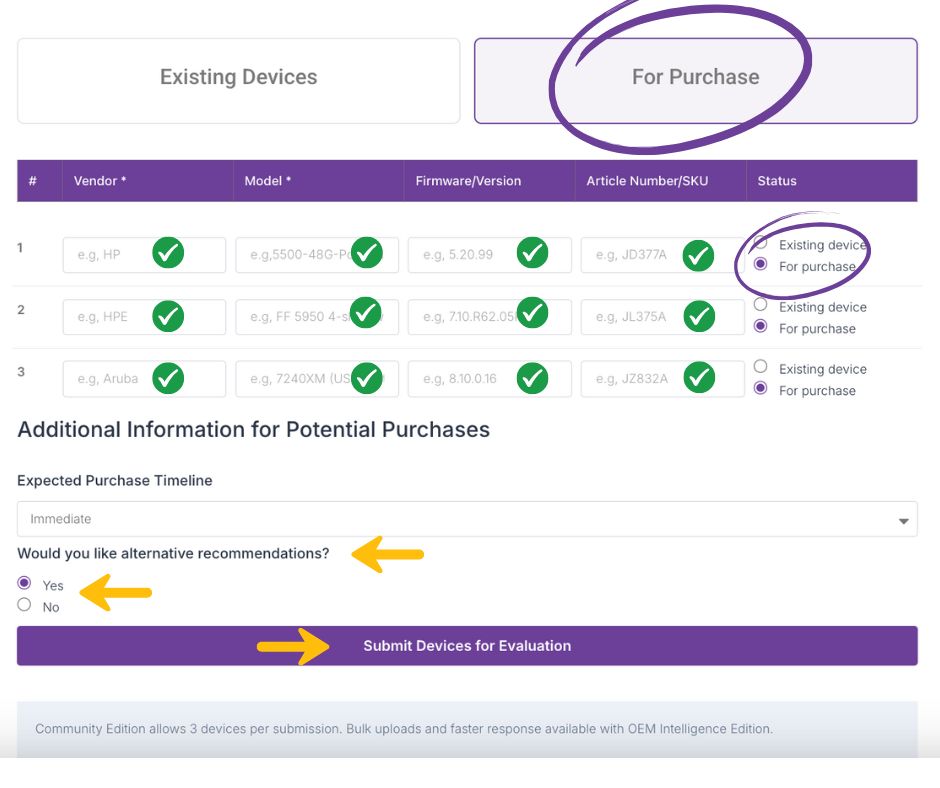
Step 3.1: Submitting Devices You’re Considering for Purchase
If you’re submitting a device you’re planning to purchase (instead of one already in use), select the “For Purchase” option.
This unlocks an optional recommendation feature that suggests alternative devices from the same category — helping you evaluate options based on security posture, vendor support, known vulnerabilities, and lifecycle status.
Ready to Try It?
Submit up to 3 devices for free and get a full risk report on your IoT, OT, network, and security devices
Useful Tip: Make Sure Your Data is Correct
The quality of your input directly affects the quality of your results.
- If you submit only a vendor and model, you’ll receive broad, version-agnostic vulnerabilities
- If you include the firmware version, we provide:
- Version-specific CVEs
- End-of-life data
- Mitigation/remediation paths
- Risk scores tied to real-world exploitability
This is the same methodology used in our full Intelligence Edition, trusted by service providers and OEMs managing healthcare, OT, IoT, and network device fleets.
Your Results: Delivered in JSON Format
Your security report will be delivered in JSON — a lightweight, structured format used across modern security and asset management tools.
Why JSON?
The data we provide is easy to parse with internal tools, making it simple to incorporate into your existing dashboards and reports. It’s designed to be compatible with your current workflows, enabling seamless integration into vulnerability management and asset tracking processes without the need for additional formatting or customization. So, let’s summarize:
- Easy to parse with internal tools
- Compatible with dashboards and reports
- Integrates into existing vulnerability and asset workflows
Whether you’re technical or not, JSON gives flexibility. Need help interpreting the results? We’ve got you.

Rockwell ControlLogix 5580: When Sources Diverge, DeviceTotal Delivers Actionable Truth

Case Study: GE Healthcare LOGIQ E10 — GE Missed Vulnerabilities on Their Own Device. DeviceTotal didn’t.
Bridging the CVE Gap: Why Organizations Can’t Rely on NVD Alone — and How DeviceTotal Closes It

How DeviceTotal Eliminated False Positives from an NVD CPE Mismatch Before the Fix Went Live

How To Submit Devices To DeviceTotal Community Edition

